
CAESAR – Republic to Empire
March 15, 2015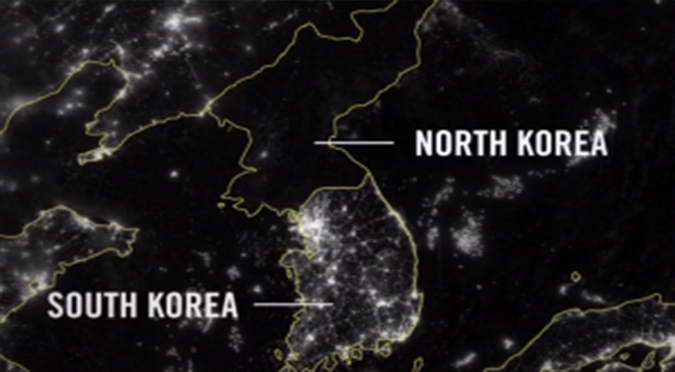
NORTH KOREA – Part One: ORIGINS
June 19, 2015CLICK HERE TO CHECK OUT THE PODCAST!
The modern world is run by technological innovation. Computers have advanced at such an incredible rate that it’s hard to imagine life without the convenience of the internet. With the advent of the World Wide Web, our ever expanding population has become more interconnected than ever before.
The Digital Age began as a new frontier of possibility. Like any other brave new era, there will always be those looking to exploit it for their own ends. From the wild west of the cyber realm emerged a new breed of cowboys and outlaws: Hackers.
Over the years, these cyber punks have been classified into two main categories: White Hats and Black Hats, those who use their powers for good… and those who don’t. The following are 15 of the most notorious exploits from this later group in chronological order…
1. Cap’n Crunch – 1972

Crunchatize me Cap’n!
John T. Draper was one of the pioneers of the cyber realm. An american programmer who first became famous for hacking into AT&T’s phone lines utilizing nothing more than a phone and a plastic toy whistle from a box of cereal. He discovered that the plastic whistle emitted a 2600 hertz tone, which was the same frequency used to override the system into operator mode.

John Draper – Evil Genius / Cereal Enthusiast
With access to the entire network, he could call anyone in the world without paying a cent. AT&T was not particularly fond of this, leading to his eventual arrest and conviction for wire fraud. John Draper became a cyberpunk legend in Silicon Valley and eventually worked with Steve Jobs and Steve Wozniak on a revolutionary dial-tone system for the Apple II Mac which made dial-up internet possible.
2. THE LEGION OF DOOM! – 1984

“The Legion of Doom” was an elite group of hackers led by “Lex Luthor”. This mysterious group of cyber enthusiasts joined forces to share knowledge and trade secrets about the loopholes of the telecommunications network. At one point the Legion had over 30 members, guys with sweet code-name’s like ‘Karl Marx’, ‘Dr. Who’, ‘X-Man’, ‘Necron 99’ and ‘Phantom Phreaker’. The hacker group quickly caught the attention of the U.S. Secret Service. A number of companies’ firewalls were infiltrated by the group throughout the 80’s, but only a handful of them were ever busted. Many of their identities remain a mystery to this day.


The quarantined Morris Worm virus.
3. THE MORRIS WORM – 1988
November 2, 1988. This was a pivotal moment in the history of cyber crimes. Robert Tappan Morris was a graduate student from Cornell University, who had developed the source code for a program intended to bypass passwords in an attempt to gauge the size and scope of the internet. Turns out he had accidentally created the first computer virus…
The program had a tiny glitch that caused itself to consistently replicate to the point of crashing entire systems with a Denial of Service error. DARPA reacted to the threat by essentially shutting down the internet and establishing CERT – the Computer Emergency Response Team to counteract future security threats. Morris was tried and was the first to be convicted of violating The Computer Fraud and Abuse Act.
(Sucks bro)
It’s estimated that the Morris Worm affected 6,000 systems and caused up to $10,000 or more in repairs.
All because of one floppy disc!

1.44 Mega Bytes of destructive power!
4. DARK DANTE vs KIIS FM – 1990
 Kevin Poulsen is a world renowned hacker who went by the alias ‘Dark Dante’ and evaded the FBI for a number of years. His most daring exploit made headlines in the early 90’s when he performed a series of expert hacks into an LA radio stations’ phone network. KIIS FM was running a contest, the station was giving away a free Porsche to the 102nd caller.
Kevin Poulsen is a world renowned hacker who went by the alias ‘Dark Dante’ and evaded the FBI for a number of years. His most daring exploit made headlines in the early 90’s when he performed a series of expert hacks into an LA radio stations’ phone network. KIIS FM was running a contest, the station was giving away a free Porsche to the 102nd caller.
Poulsen decided to rig the contest by blocking all other incoming calls ensuring that he was the owner of a brand new Porsche 944 S2 sports car. But he didn’t stop there, he continued to hack the station and calling in under different personas, eventually winning over $20,000 cash, two Hawaiian vacations, and ANOTHER Porsche!
Because of course he did.
Eventually the FBI did catch up with Poulsen when he was recognized at a supermarket, after being featured on the show “Unsolved Mysteries”. It probably didn’t help that he hacked the Bureau’s files on several occasions. He was arrested, prosecuted and charged with money laundering and wire fraud. Many years since he’s served his time, Kevin Poulsen has since become a respected journalist, writing about cyber security for Wired magazine.
5. SOLAR SUNRISE – 1998

In the late 90’s, a trio of teenage hackers exploited a security loophole in the Solaris operating system and initiated a systematic cyber attack on over 500 private AND government computers. They used a virus to gain access to and seize control of numerous computer systems at NASA and the Pentagon. The security breach was so severe that President Clinton was briefed on the situation. Fearing the worst, the FBI and CIA launched a worldwide investigation. Officials were surprised to discover the identity of the perpetrators: two kids from California with the help of a 19 year old Israeli hacker known as… ‘Pink Pony’?!

Somehow much less threatening than I expected…
6. @MafiaBoy – 2000
 A Canadian hacker by the handle of “MafiaBoy” took the world by storm on February 7, 2000, when the top search engine at the time, Yahoo (not Google), was shut down for an entire hour!
A Canadian hacker by the handle of “MafiaBoy” took the world by storm on February 7, 2000, when the top search engine at the time, Yahoo (not Google), was shut down for an entire hour!
It didn’t stop there though, DDoS attacks continued across the web: Amazon, CNN, and Ebay were all taken out by server overloads. This campaign of cyber warfare, dubbed ‘Project Rivolta’, caused an estimated $1.2 BILLION in damages!
It’s perpetrator, MafiaBoy was a ghost… that is until he started bragging about his exploits on message boards and chat rooms. The FBI soon discovered his identity: 15 year old Michael Calce.
7. THE NIMDA VIRUS – 2001

On September 18, one week after the 9-11 attacks, one of the most powerful viruses yet was unleashed on the web: The Nimda Virus. (‘Nimda’ being ‘Admin’ backwards) Within just 25 minutes of it’s release on the web, this multi-vector worm spread throughout the US, affecting Windows 95, 98, Me, Nt, 2000 and XP. It was by far the most widespread and destructive virus of it’s time, costing approximately $2.6 billion. Mike Sher compared counteracting the virus to fighting a forest fire. Although it’s origins have never been officially confirmed, evidence suggests that Chinese hackers were in fact behind the coordinated attack.
8. #SoBIG.F – 2003

SoBIG.F was one of the most widespread and destructive Trojan worms of all time, infecting over 2 million PC’s worldwide and causing damages upwards of $37 BILLION DOLLARS! That’s waaay more money than your average Super Villain holds the world ransom for! This viral monstrosity spread via e-mail spam. At first the worm was deployed from Big@boss.com under various subject lines of false pretenses, but then once it infected a computer, it would send itself out to ALL the e-mail contacts in the infected user’s address list.

The insidious creator of this nefarious software is still at large… and needs a good kick in the &#$%
9. THE SLAMMER – 2003

Just a few weeks after ‘SoBig’ was released, another bot net worm was unleashed on an unsuspecting public: “The Slammer”!
This virus took advantage of a loophole in Microsoft’s SQL server and managed to infect HALF of ALL internet servers in just 15 minutes! 75,000 unpatched routers and 200,000 Pc’s were affected, causing roughly $1.2 billion, but that’s not all, this time things got serious: Bank of America ATM’s, Continental Airlines flights, Seattle’s 911 network, and even a nuclear power plant in Ohio were all compromised. The government intervened and managed to contain the spread of the virus, but it’s creator disappeared without a trace…

Speaking of Slammers, anyone else remember pogs?
10. THE ‘MYDOOM’ TROJAN – 2004
Like many of the previous cyber attacks listed, the “MyDoom” virus came out of nowhere. This ‘parasitic’ worm affected 2 million pc’s, caused an absurd $38 billion in damages, and did what no hacker could ever do before: it shut down Google for a day. It’s creator is still unknown, but there have been many conspiracy theories circulating, from a Russian cyber attack to an inside job to demonic beings from the nether-realm.

11. MAX VISION – 2006

Highway to the Danger Zone!
Going by the alias of ‘Iceman’ from his safe-house in San Fran, former security researcher, Max Vision went rogue.
(Mad) Max hacked into, absorbed, and wiped out several cyber fraud sites and then proceeded to use the stolen data to create his own brand of internet black market. His site, ‘The Carders Market’, became one of the largest online criminal marketplaces where stolen identities were bought and sold. With his extensive criminal past, it didn’t take long for the authorities to put the pieces together.
He was soon caught and arrested by the FBI. Max Vision was charged with two counts of fraud, the theft of 2 MILLION credit card numbers, and $86 million in fraudulent charges. Not cool bro, not cool.
He’s currently serving a well deserved sentence till 2019.
12. STUXNET – 2010

In 2010, ‘Stuxnet’, one of the most sophisticated computer viruses ever created, was let loose and the world would never be the same again…
This unprecedented malware was specifically engineered to stealthily infiltrate and cause physical damage to the operating system of a nuclear power plant. Essentially, it was the first weaponized computer virus… and it was created by the United States in an effort to put a monkey wrench in Iran’s nuclear program.
The virus went undetected for months until inspectors from the International Atomic Energy Agency made a visit to Iran’s Natanz uranium enrichment plant, and noticed that they’re centrifuges were catastrophically failing. It wasn’t until month’s later, when computers around the country were consistently crashing and rebooting that the digital warhead was discovered. And it all started with an infected flash-drive.
The scary thing is, this virus is out there now, in the back alleyways of the internet, just waiting for a cyber terrorist to take advantage of it.
13. THE TARGET CREDIT HEIST – 2013

November 27th, 2013 – a couple days before Black Friday, the Target corporation became a target for data thieves.
 The hacks went undetected for a number of days. Over the course of the next few weeks, over 40 million credit and debit cards had been compromised and personal information for over 70 million customers had been stolen! One Third of all American consumers were affected. The retail giant unfortunately didn’t discover the security breach until December 15th, and waited until the 19th to inform the public. Although the malware was eventually detected and removed, the damage had already been done. This was an unprecedented breach in cyber security.
The hacks went undetected for a number of days. Over the course of the next few weeks, over 40 million credit and debit cards had been compromised and personal information for over 70 million customers had been stolen! One Third of all American consumers were affected. The retail giant unfortunately didn’t discover the security breach until December 15th, and waited until the 19th to inform the public. Although the malware was eventually detected and removed, the damage had already been done. This was an unprecedented breach in cyber security.
Security specialists in India actually discovered suspicious activity and alerted Target’s operation center in Minneapolis a number of times, but the alerts somehow went undetected while hackers were trading card numbers on the black market. The hackers raised about $53.7 million from fraudulent transactions.

It turns out that Target wasn’t the only one hit, a number of companies including Home Depot, UPS, JP Morgan, and several other companies that decided to remain anonymous. The FBI and INTERPOL were soon involved in hunting down the perpetrators.
This digital heist / mass identity theft was eventually traced to Russia, where a 17 year old kid from St. Petersburg, Sergey Taraspov was said to have created the program that infiltrated Target’s cash registers. 23 year old Rinat Shabayev was said to have helped sell the malware online to other cyber criminals. There have been dozens of related arrests world wide.

On a personal side note: I was actually working for Target at the time, in the worst place possible – guest services, where I dealt with an onslaught of angry house wives and confused grandpas who didn’t seem to understand that I wasn’t the one who had hacked them, nor was I going to give them a refund for their stolen credit card information, but that they could contact their banks and then complain to corporate, whilst being told by my boss to push Red Cards… It really just sucked for everybody.
14. THE SONY HACK – 2014

On November of 2014, Sony Pictures Entertainment became the victim of one of the most savage hacker attacks ever. Over 100 TERABYTES (!) of data was stolen, including: scripts, leaked movies, countless private e-mails, social security numbers, and the personal information of 47,000 employees AND their families! – all of which was dumped online.
 Within this massive data dump, a lot of damaging information came to light about the film company’s inner workings, including: some racist comments between producers concerning certain demographics, the fact that there were lay offs in order to outsource overseas special effects work, one of their major productions had gone insanely over-budget, and multiple leaked movies and scripts.
Within this massive data dump, a lot of damaging information came to light about the film company’s inner workings, including: some racist comments between producers concerning certain demographics, the fact that there were lay offs in order to outsource overseas special effects work, one of their major productions had gone insanely over-budget, and multiple leaked movies and scripts.
An anonymous group of hackers came forward, claiming responsibility: ‘The Guardians of Peace’ aka the GOP (not to be confused with the other equally dubious organization). In their bold statement, the group threatened any movie theater that would be premiering the Seth Rogan / James Franco comedy, “The Interview”, a satire about two dudes who infiltrate North Korea to assassinate Kim Jong-un.

“All the world will denounce the SONY!” – actual quote from the GOP.
Adding more fuel to the fire, Kim Jong-un himself threatened war against the US over the film’s release. Sony initially caved and pulled the movie from release, but on Christmas Eve, decided to release the movie for download and streaming through various outlets, including Netflix and Xbox Live. All evidence points to North Korea being behind the Sony hacks, including IP addresses and its similarity to cyber attacks on South Korea, but some security experts think it was all a diversion from the real culprits, perhaps some former disgruntled employees.
The history of North Korea – Part One
15. CODE-NAME: CARBANAK – 2015
Earlier this year, the largest digital heist of all time was carried out by an international gang of cyber thugs.
Over $1 billion from at least 100 banks in 30+ countries was reportedly stolen! The bank servers were infected with a cutting-edge malware known as “Carbanak”, which would infect a bank’s systems over the course of a few months and record confidential transaction numbers in order to manipulate the cash flow elsewhere. These cyber criminals, many from Russia and around Europe, had various methods. Some would steal from various banks around the globe through fraudulent transactions and deposit the stolen money in China, while others would hack individual ATM machines.

Looks like these guys are out of a job.
ERIK SLADER
Hope you enjoyed this edition of “Epik Fails of History!”, if you have any questions, concerns, or suggestions let me know in the comments below! Also, be sure to ’Like’ EPiK FAILs on Facebook, or Follow on Twitter, and SHARE IT with your friends!
—– More articles on Historic Failure:
 Y2K – A Day that shall live in Mockery
Y2K – A Day that shall live in Mockery
ENRON – A Conspiracy of Corporate Corruption
Blockbuster, Borders, and Bankruptcy!
13 of the Worst Ecological Disasters of All Time
NORTH KOREA – Part One: Origins
—Sources:
http://www.wired.com/2014/11/countdown-to-zero-day-stuxnet/
http://www.cnn.com/2014/01/20/us/money-target-breach/
 http://malware.wikia.com/wiki/Sobig
http://malware.wikia.com/wiki/Sobig
http://malware.wikia.com/wiki/Nimda
http://en.wikipedia.org/wiki/Legion_of_Doom_%28hacking%29
http://www.wired.com/2009/12/ye_cybercrimes/
http://www.itsecurity.com/features/top-10-famous-hackers-042407/
http://articles.latimes.com/1993-09-12/magazine/tm-34163_1_kevin-poulsen
http://computer.howstuffworks.com/worst-computer-viruses.htm
http://en.wikipedia.org/wiki/Sony_Pictures_Entertainment_hack#Information_obtained
http://www.arnnet.com.au/slideshow/341113/top-10-most-notorious-cyber-attacks-history/?image=8
http://www.thedailybeast.com/articles/2014/12/20/sony-hackers-guardians-of-peace-troll-fbi-fbi-is-the-best-in-the-world.html
http://www.ibtimes.com/hackers-steal-1-billion-biggest-bank-heist-history-could-they-take-down-whole-system-1818010






6 Comments
[…] Top 15 Most Infamous Cyber Crimes! […]
[…] Top 15 Most Infamous CYBER CRIMES! […]
[…] threatened the United States once again… because they made fun of him. Many believe that the Sony Pictures cyber hacks (by an anonymous group calling themselves ‘The Guardians of Peace’) were either North […]
[…] 13 of the most Infamous DIGITAL HEISTS! […]
[…] Also be sure to check out the original blog article on the 15 Most Infamous Cyber Heists of All Time… […]
[…] *Also be sure to check out the original blog article on the 15 Most Infamous Cyber Heists of All Time… […]